Cloudflare Zero Trust
Connect ConfigCat with Cloudflare Zero Trust via SAML.
Introduction
Each SSO Identity Provider requires specific information to configure a SAML integration. The following guide will walk you through how you can connect ConfigCat with Cloudflare Zero Trust as a SAML Identity Provider.
1. Create an Application in Cloudflare
-
Log in to CloudFlare, go to the Zero Trust dashboard, and select
Applicationsunder theAccessmenu.
Then click onAdd an application.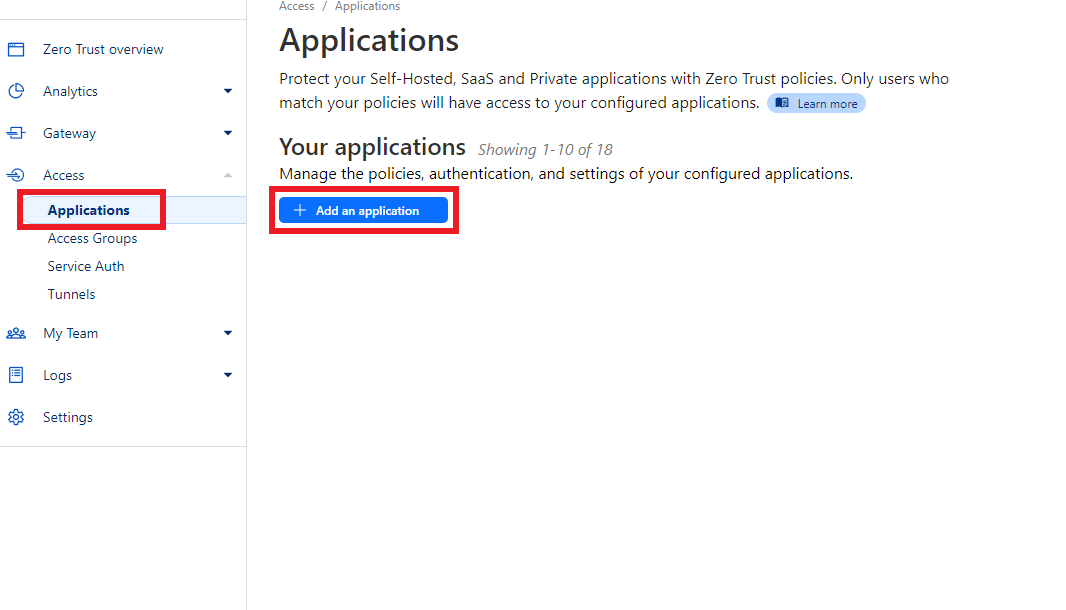
-
Select
SaaS.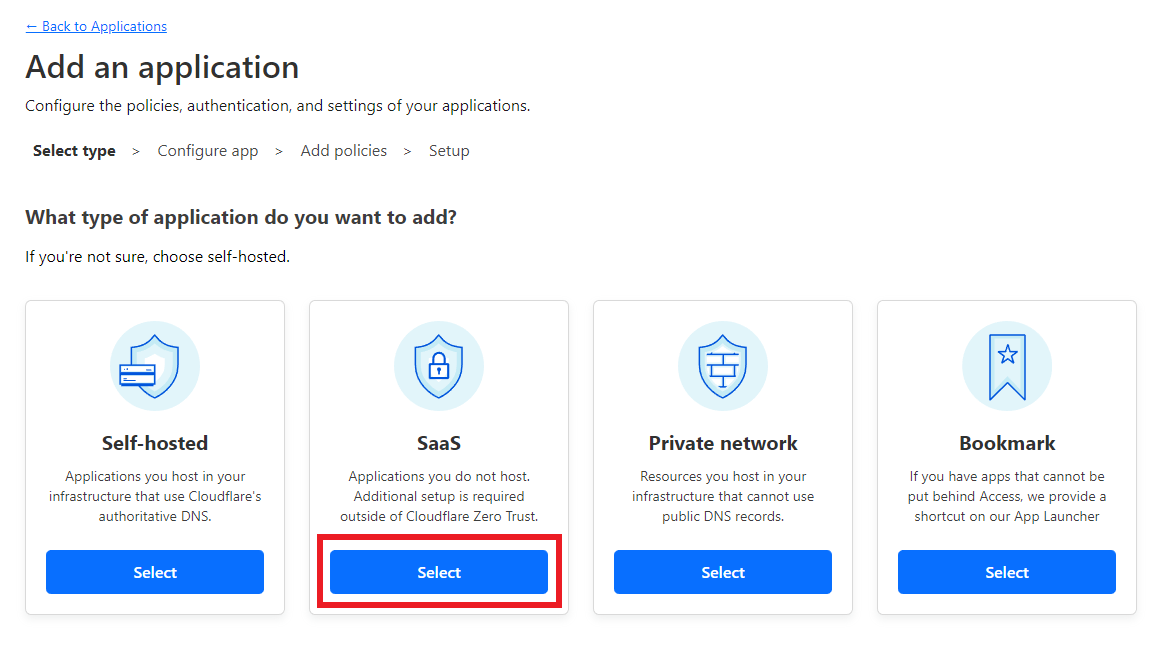
-
Enter a descriptive name in the
Applicationfield.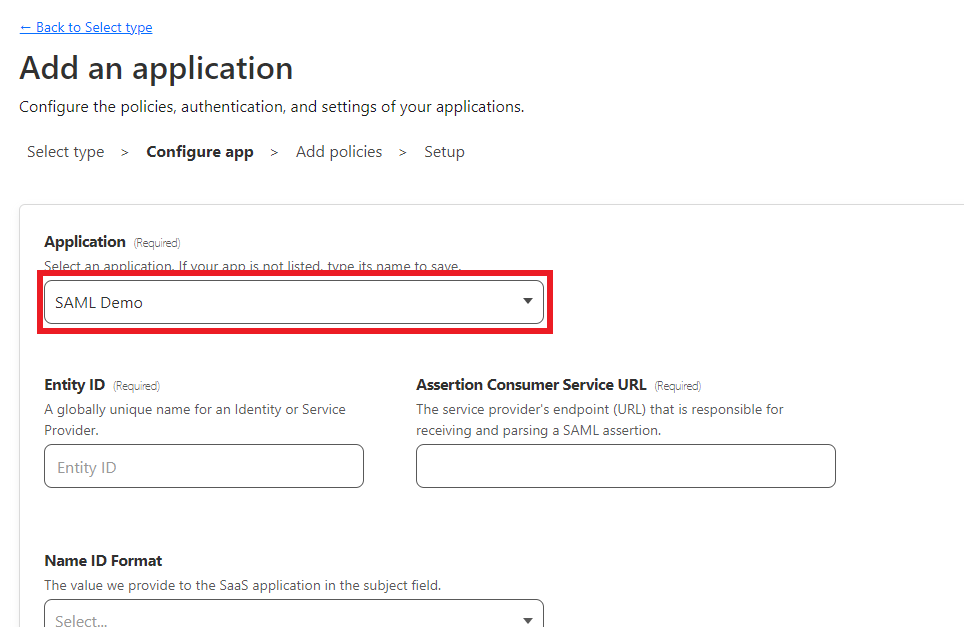
The next step will guide you on how to collect the information required for the appearing configuration section.
2. Configure SAML for the Cloudflare Application
-
Open your organization's authentication settings on the ConfigCat Dashboard.
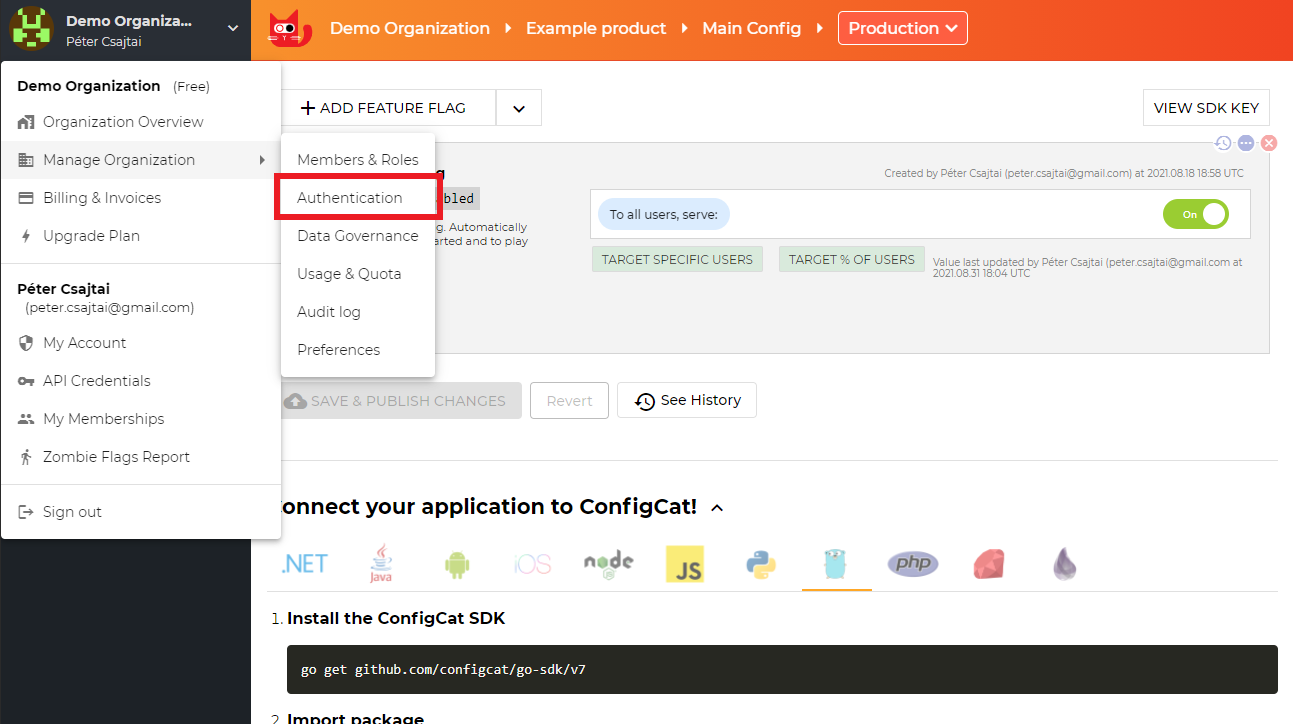
-
Click
ADD SAML IDENTITY PROVIDER.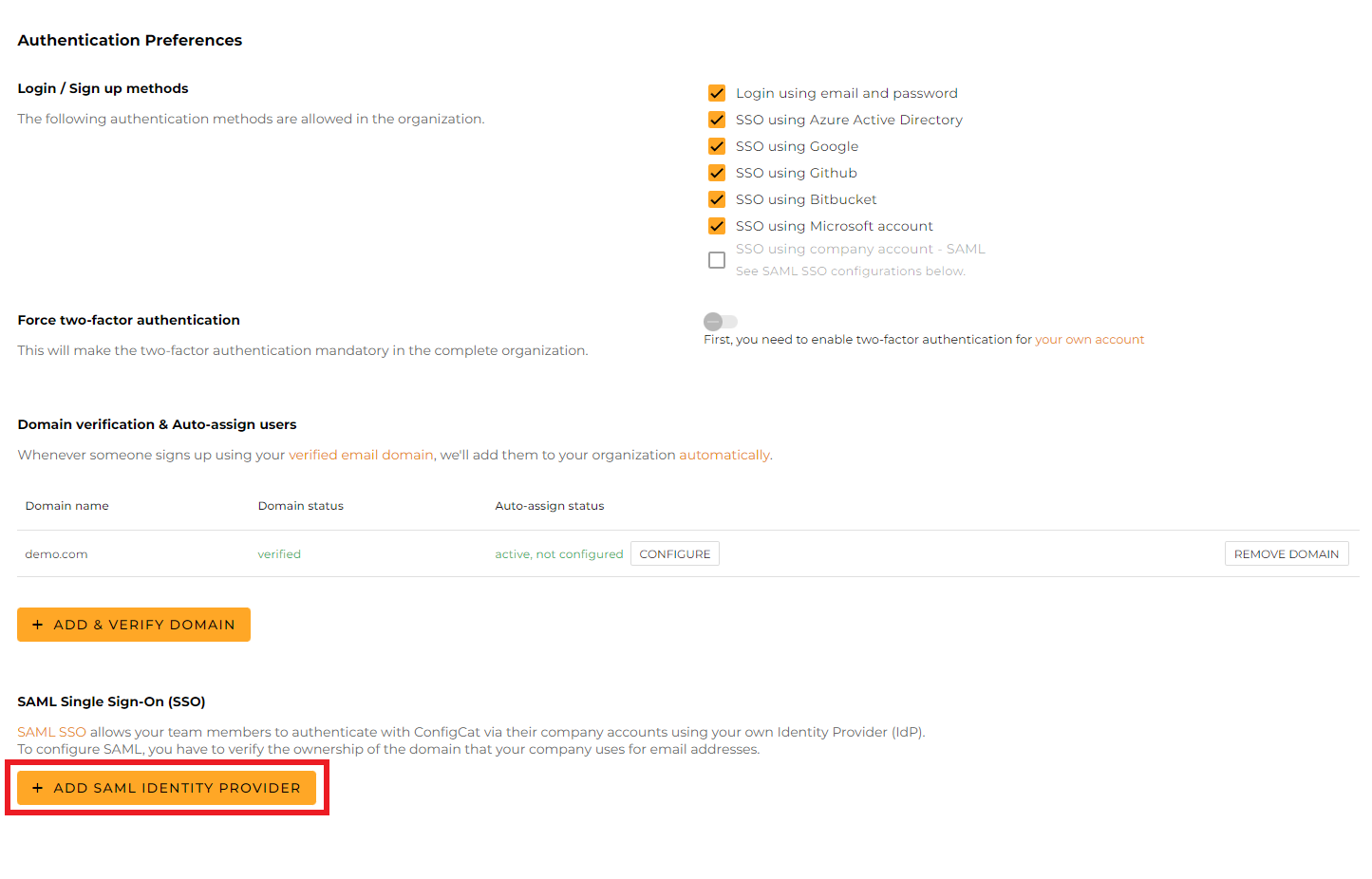
-
Give a name for your Identity Provider, and click
Create.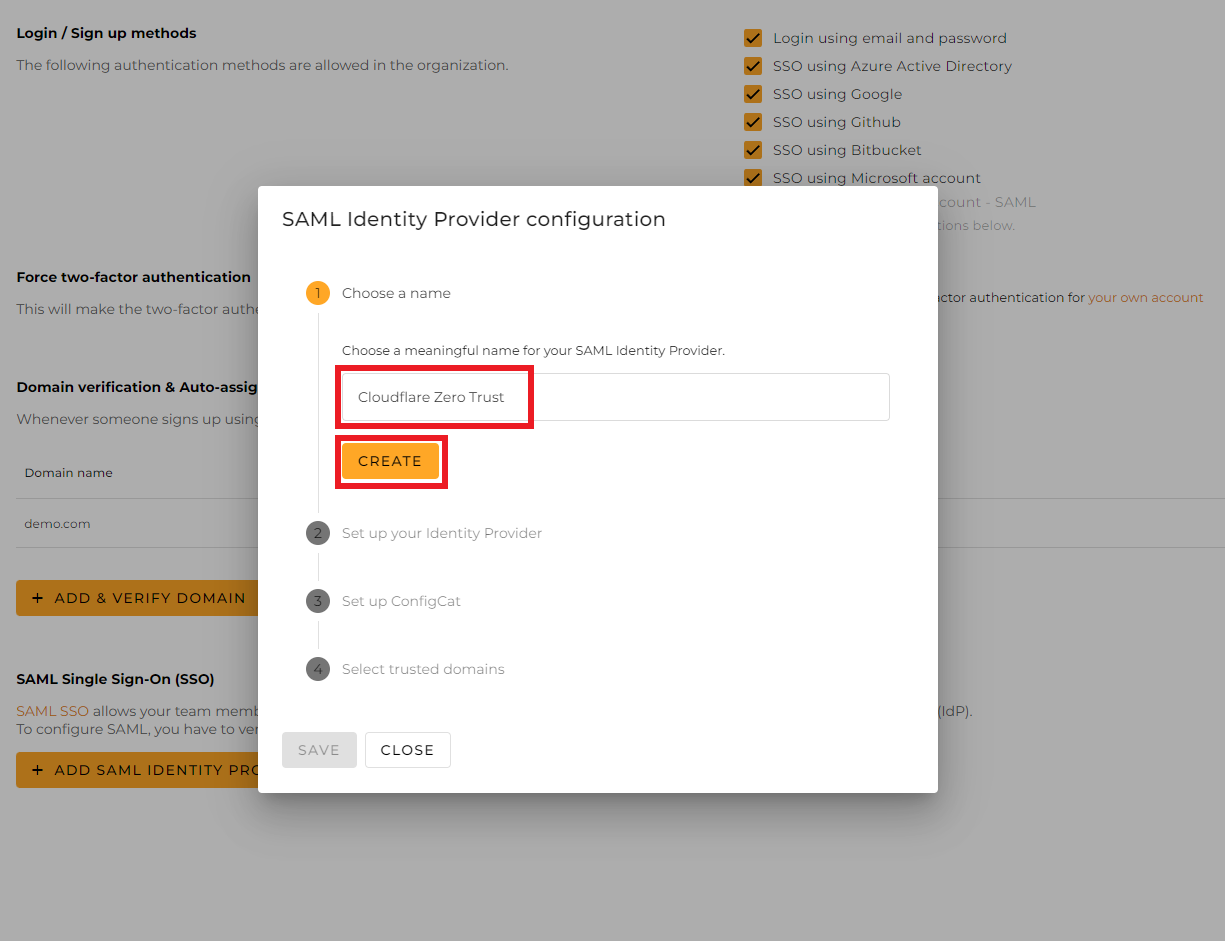
-
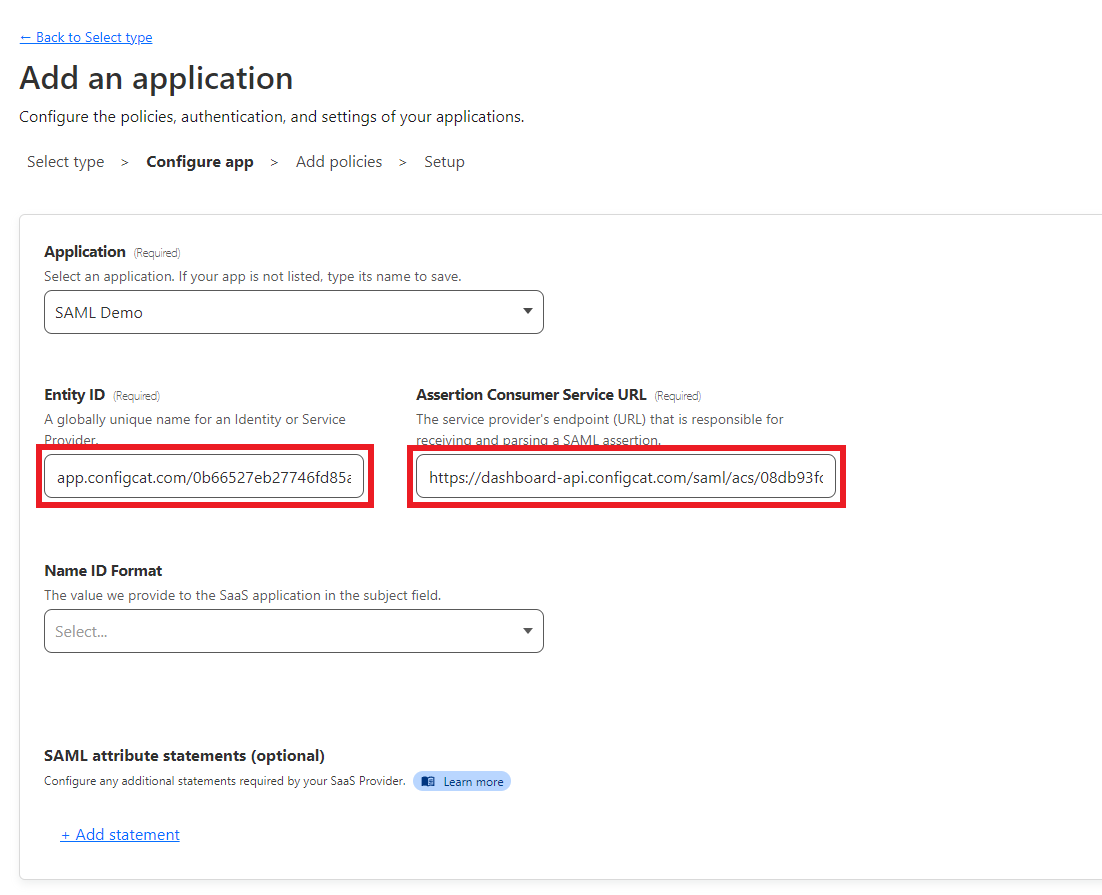
From the next section of the dialog, copy the following values and paste them into the Cloudflare application.
-
Entity ID->Entity ID -
Assertion Consumer Service->Assertion Consumer Service URL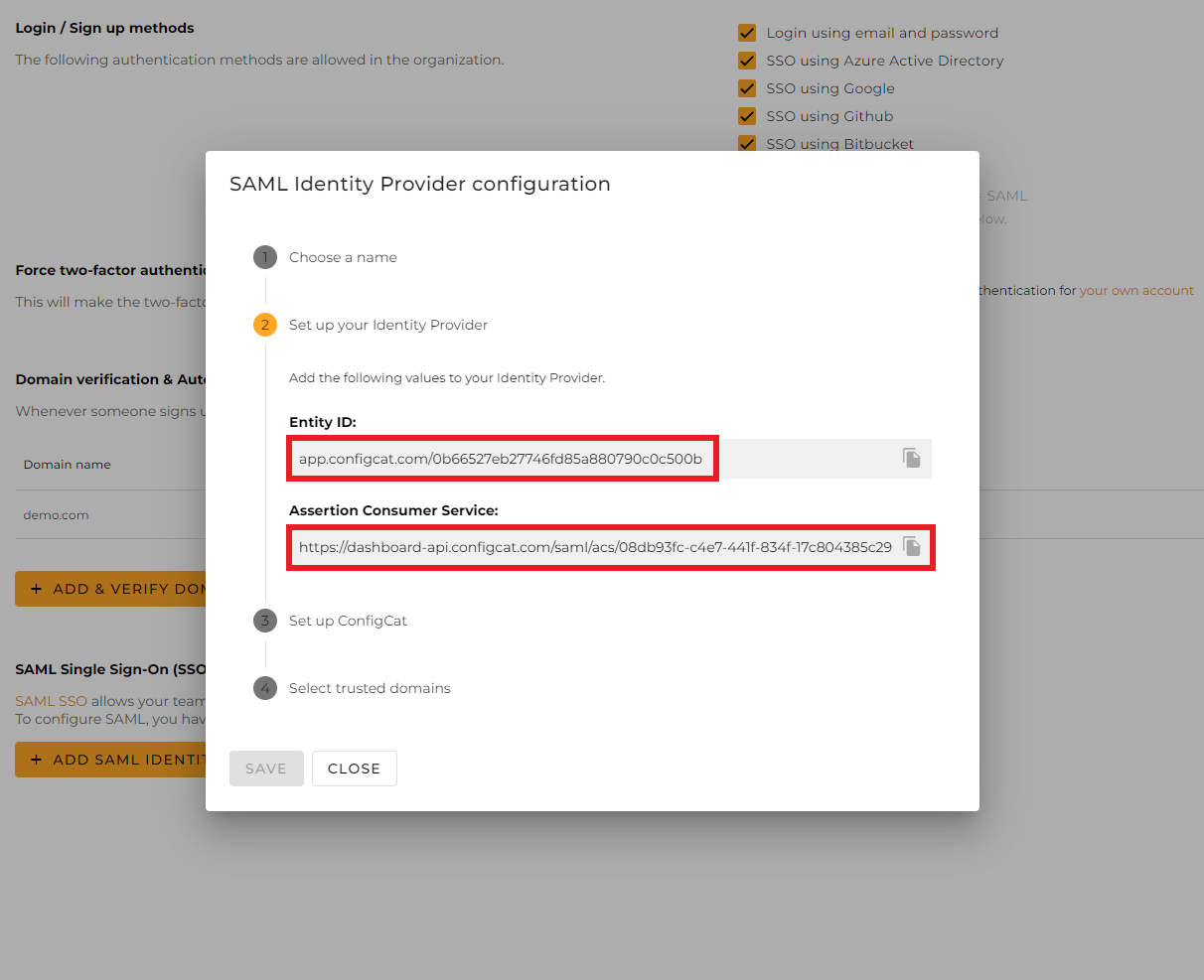
-
-
Set the
Name ID FormattoEmail.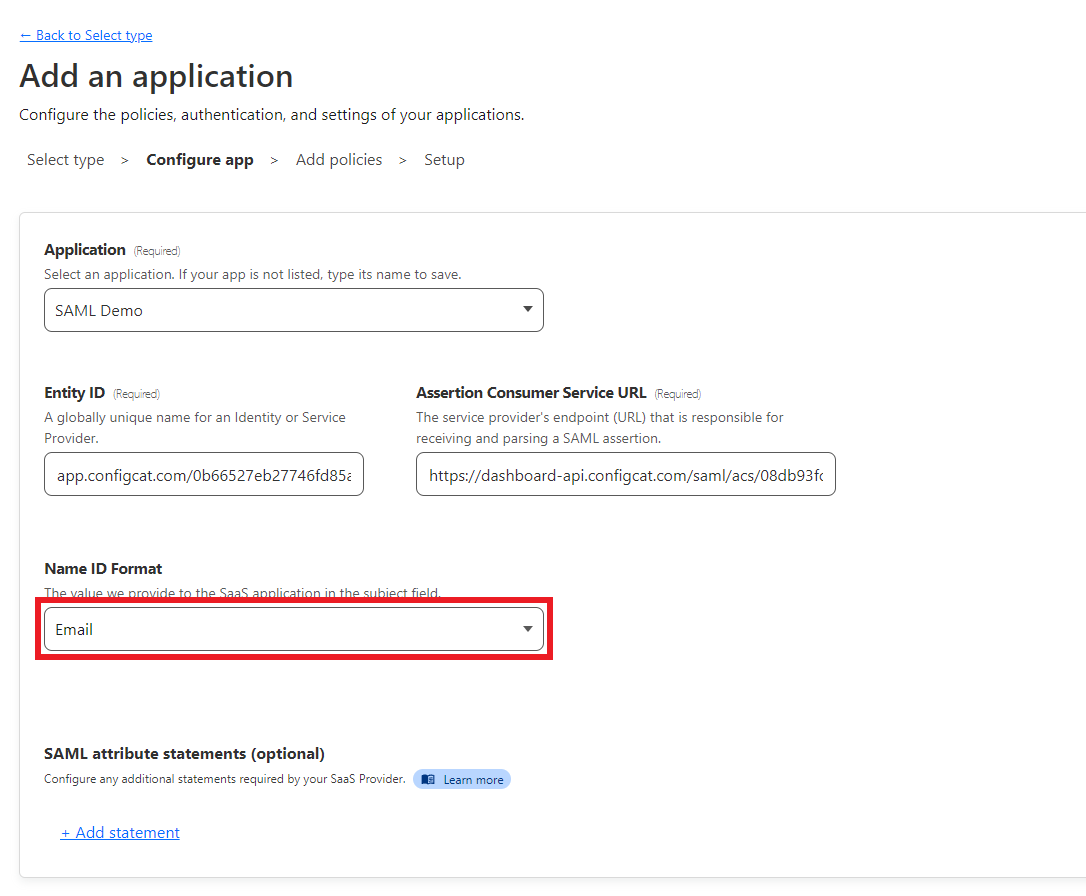
-
Click
Nextat the bottom of the page.
3. Configure policies for the Cloudflare Application
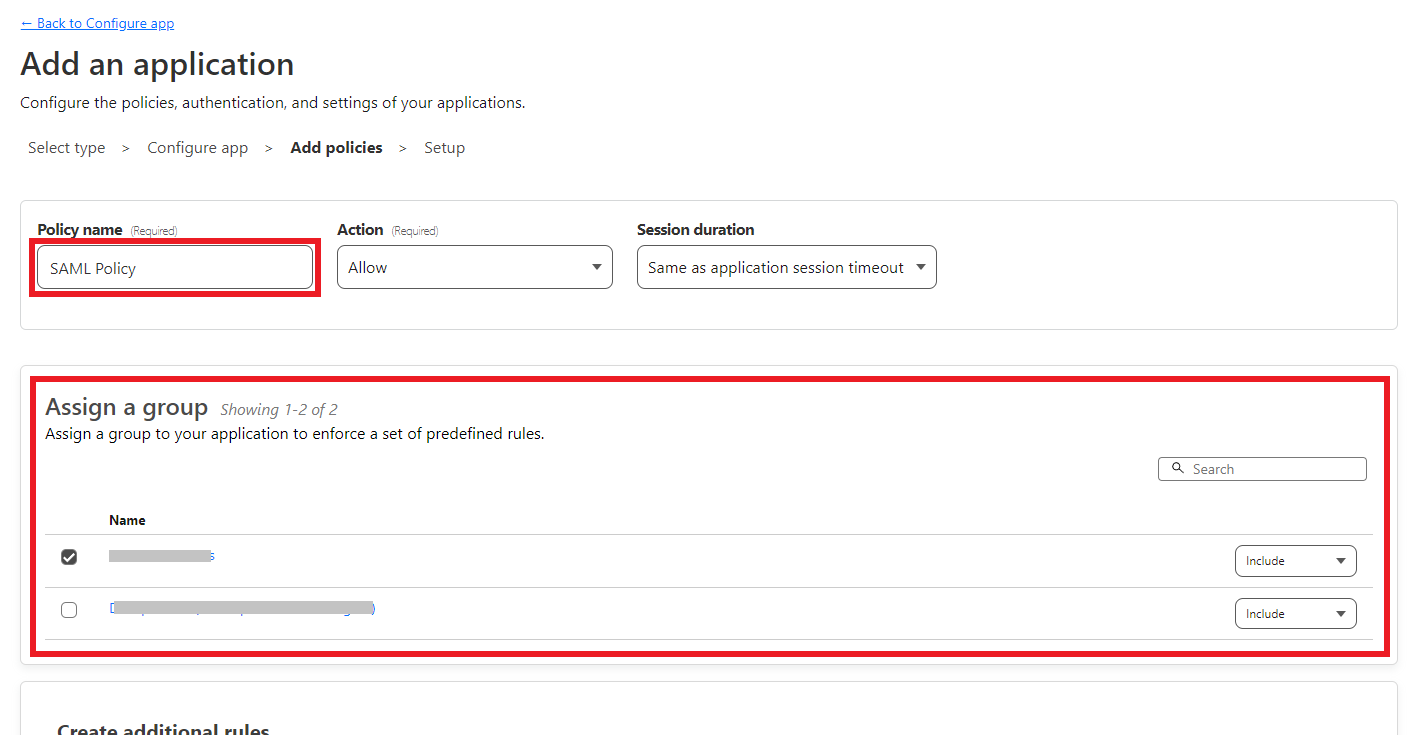
To let users authenticate via SAML, you need to assign groups to the Cloudflare application.
-
Give a name for the Cloudflare Application's policy and check those groups that you want to assign.
-
Click
Nextat the bottom of the page.
4. Configure ConfigCat with SAML Details from Cloudflare
-
Copy the value of
SSO endpointandPublic keyfields.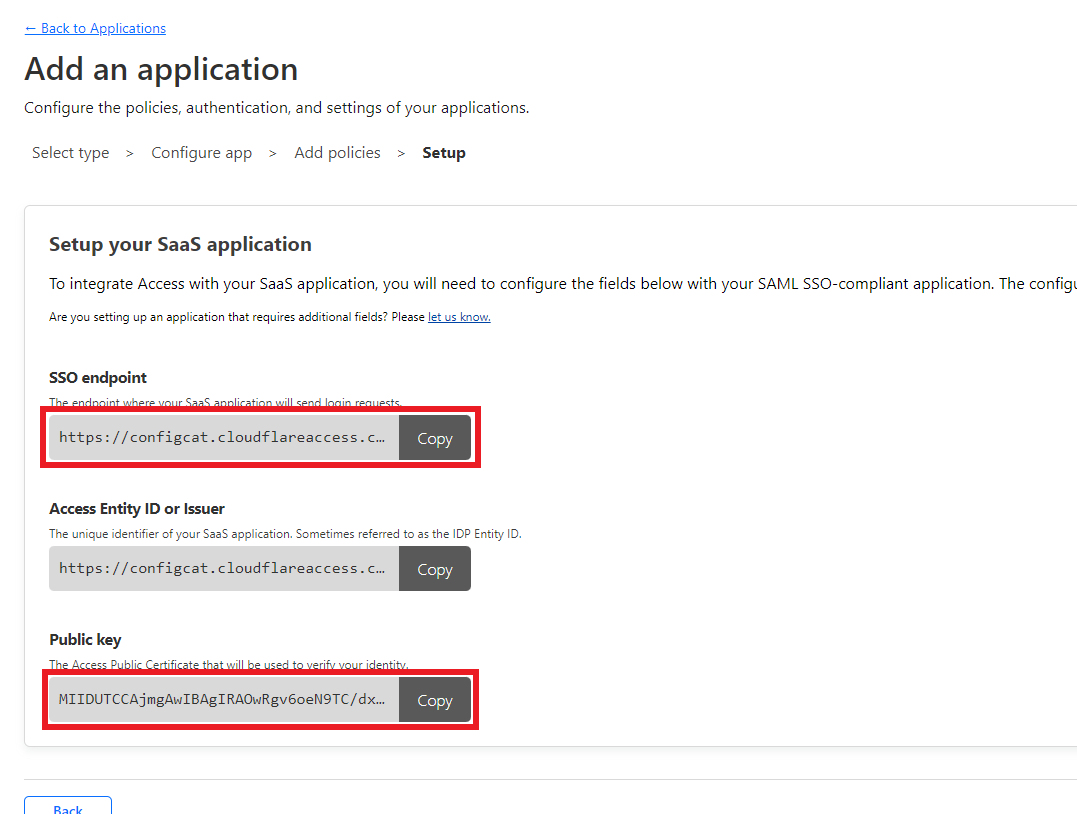
-
On the ConfigCat Dashboard, select the
3. Set up ConfigCatstep, clickManual Configuration, then paste the copied values into the appearing fields.-
SSO endpoint->Sign-on URL -
Public key->X.509 Certificate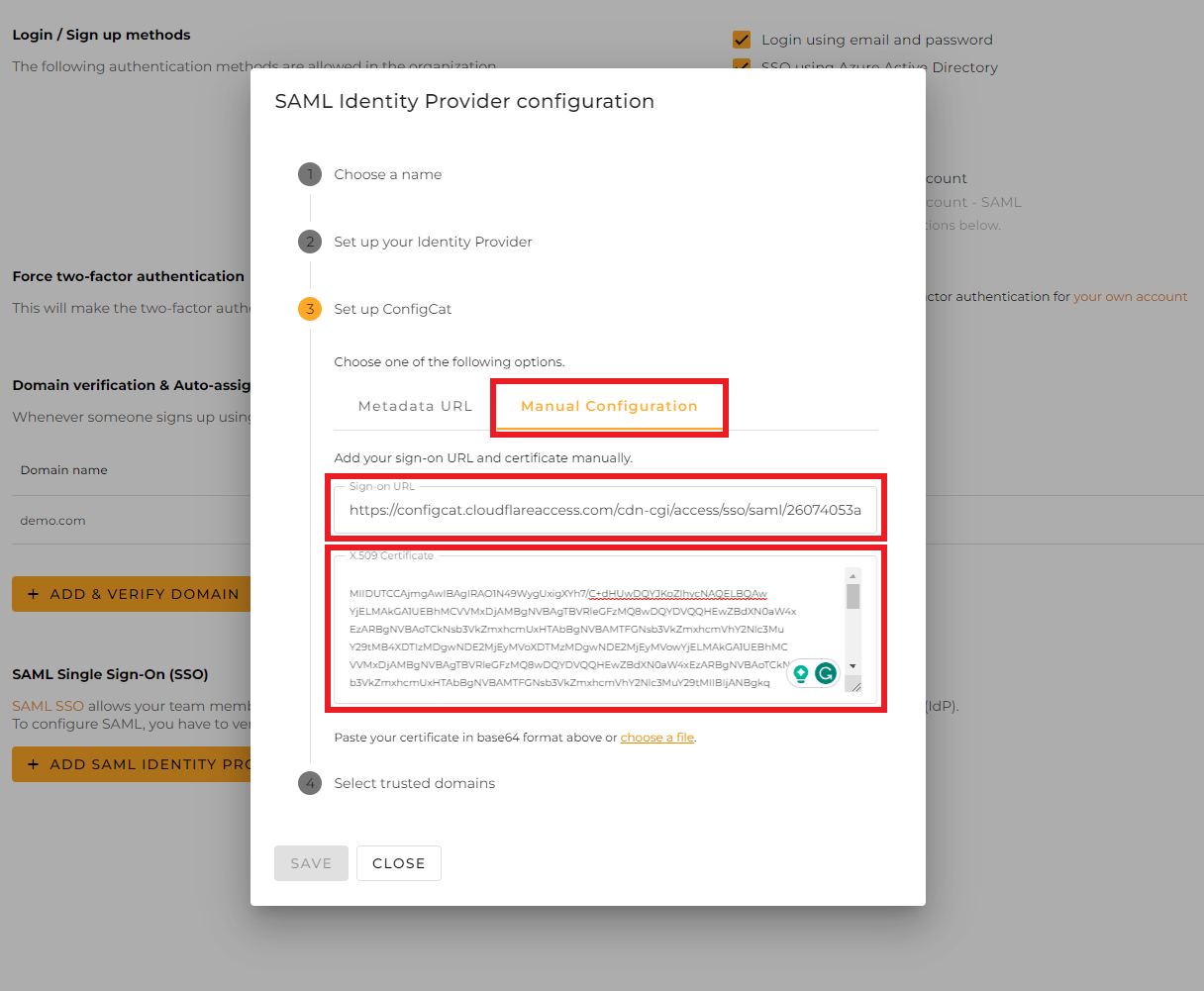
-
5. Select Trusted Domains on the SAML Configuration Dialog
-
Only user accounts from trusted domains can login with SAML SSO. You can bind multiple verified domains to a SAML Identity Provider.
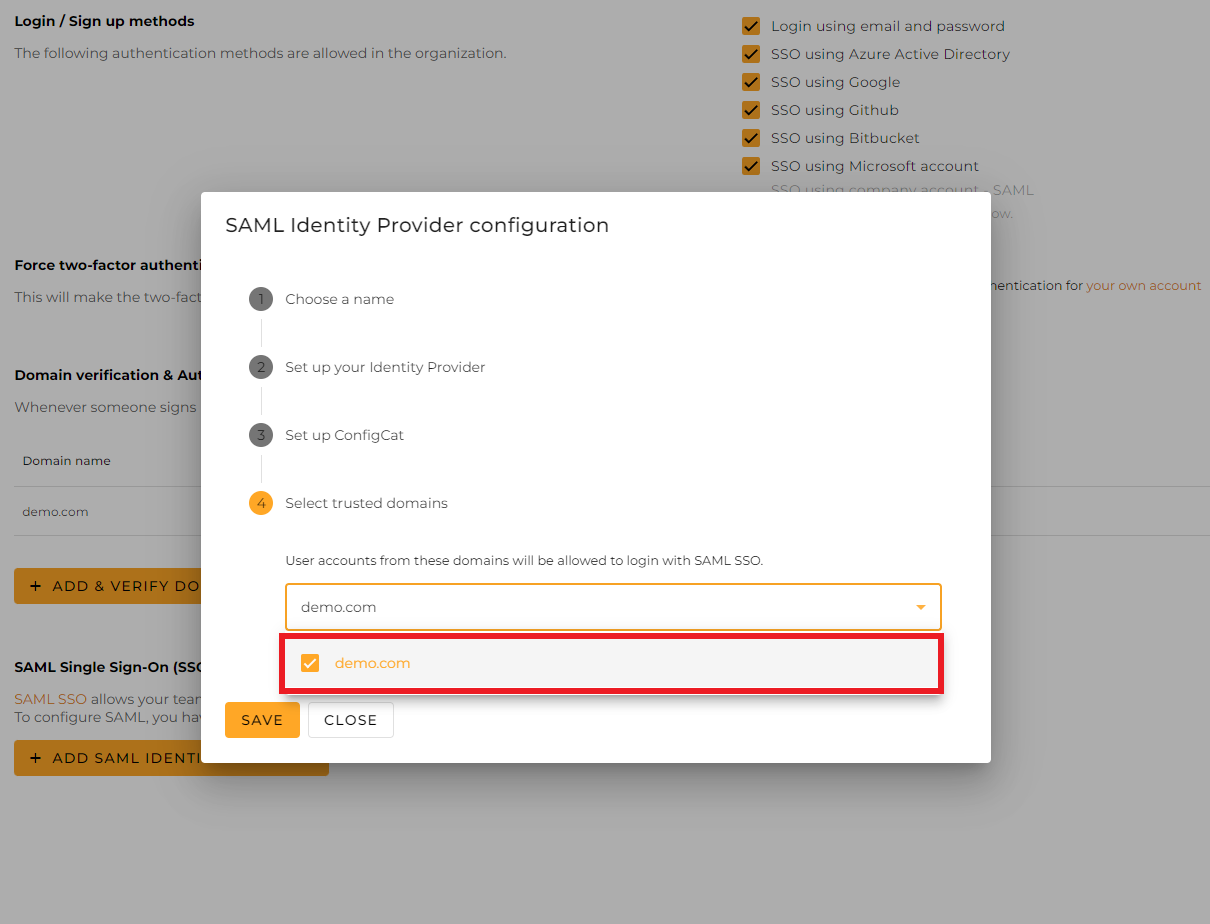
-
Click
Save.
5. Sign In
-
Go to the ConfigCat Log In page, and click
COMPANY ACCOUNT - SAML.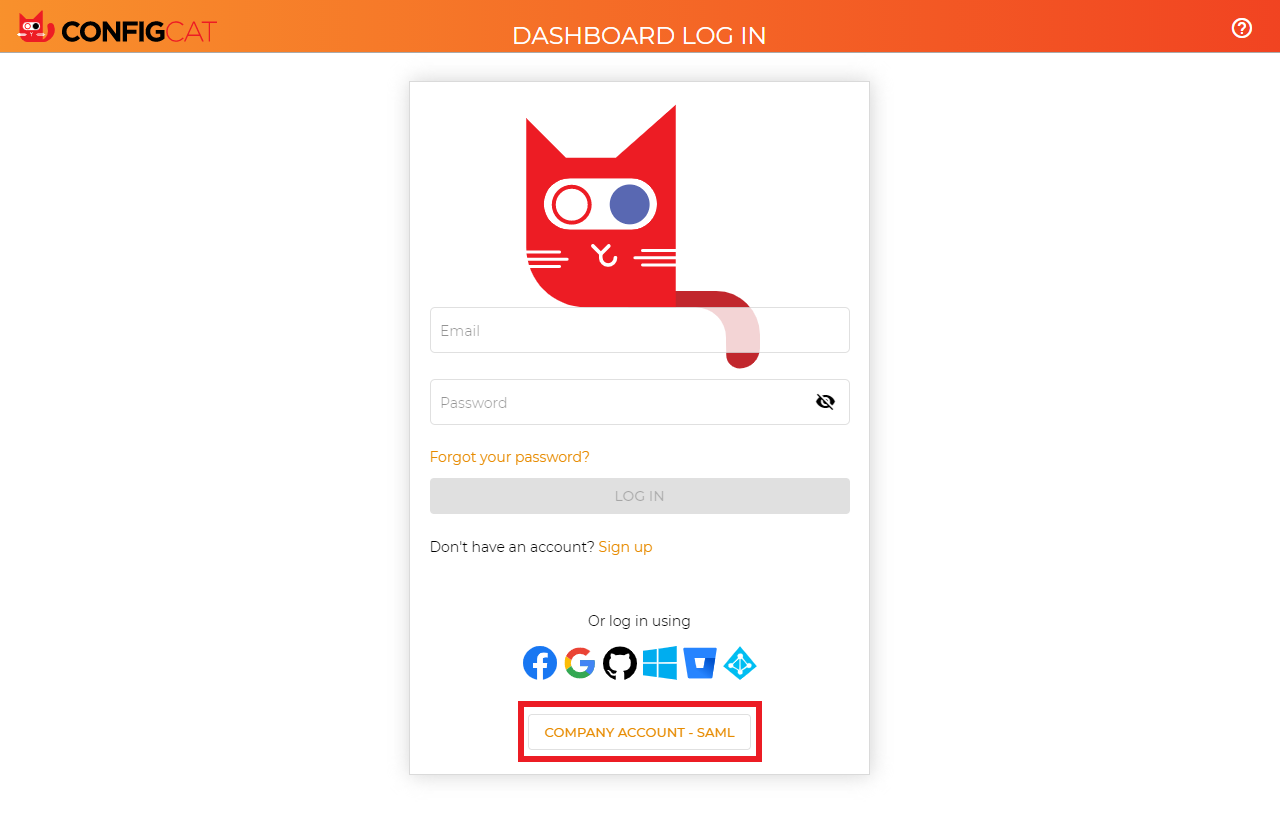
-
Sign in with your company email address assigned to the Cloudflare application.
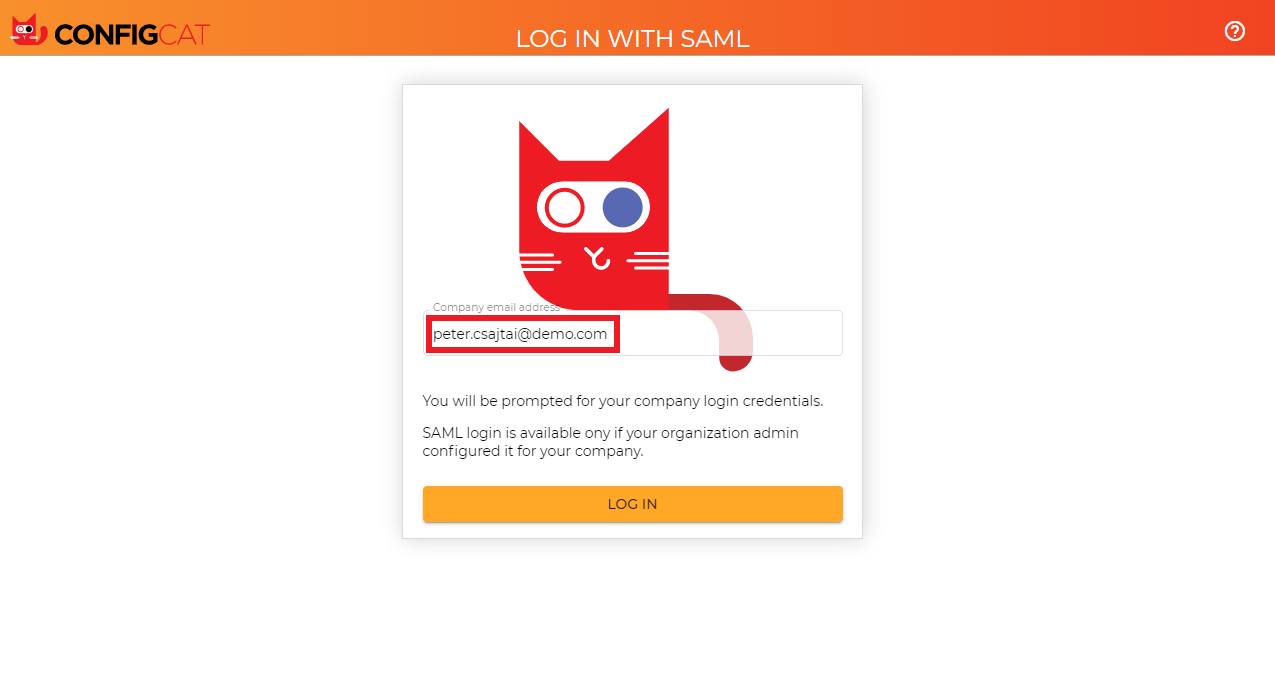
-
ConfigCat will redirect you to Cloudflare's sign in page.

6. Next Steps
- Configure the auto-assignment of users.